Research
Users want a unified identity security tool with the right protocols and time based controls baked in.
I partnered with our UX researcher to better understand how users were managing shared SaaS accounts in their current workflows. Through research, we spoke to 11 developers and DevOps engineers through user interviews.
Problem framing
I facilitated a workshop to align our stakeholders on the problem space and identify high risk areas.
I ran a 2 day workshop with engineers, engineering manager, PMs, and our UX researcher. The workshop was broken up into different activities including knowledge sharing, problem framing, brainstorming, risks, and journey mapping.
Workshop outcomes
Design challenge
How might we allow admins to securely manage shared accounts while enabling end users to access credentials with full auditability?
Success metrics
To ensure we are delivering value, we came up with metrics to track adoption, compliance, and engagement.
To align the team and measure impact, we defined a set of product and UX success metrics.
Iterations
Practiced divergent thinking to explore potential solutions for policies.
I explored multiple variations of the policy rule creation form and partnered with engineering and PMs to gather product and feasibility feedback. Through iterative collaboration, we refined the designs and aligned on the final version shown below.
Final solutions
A unified identity security tool for managing, delegating access, and retrieving account credentials.
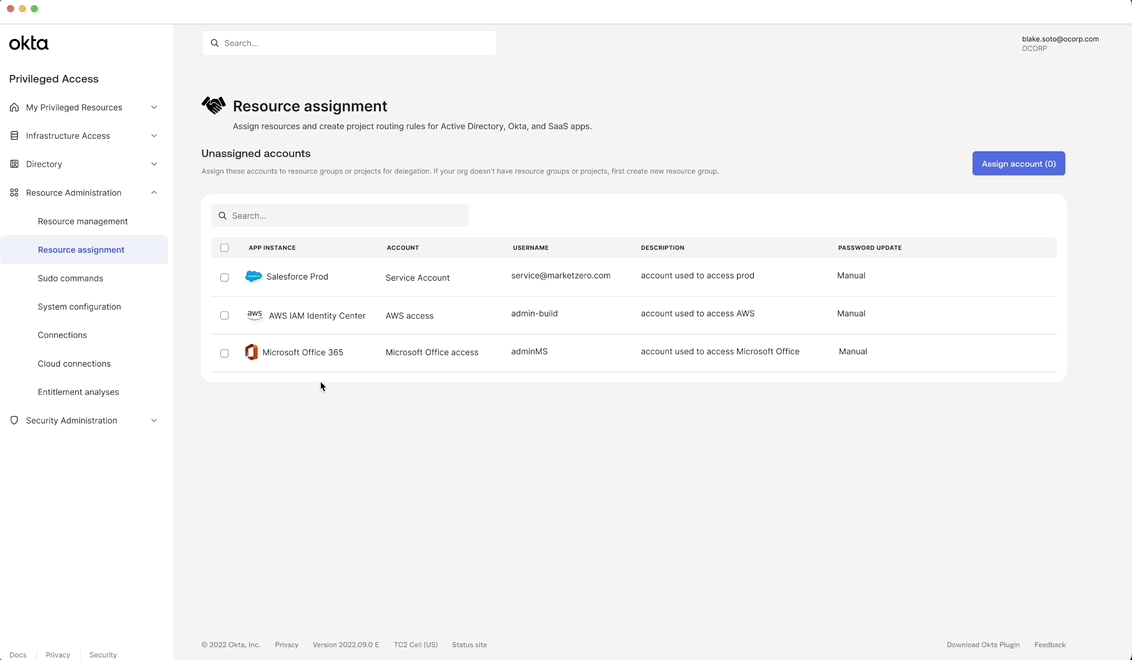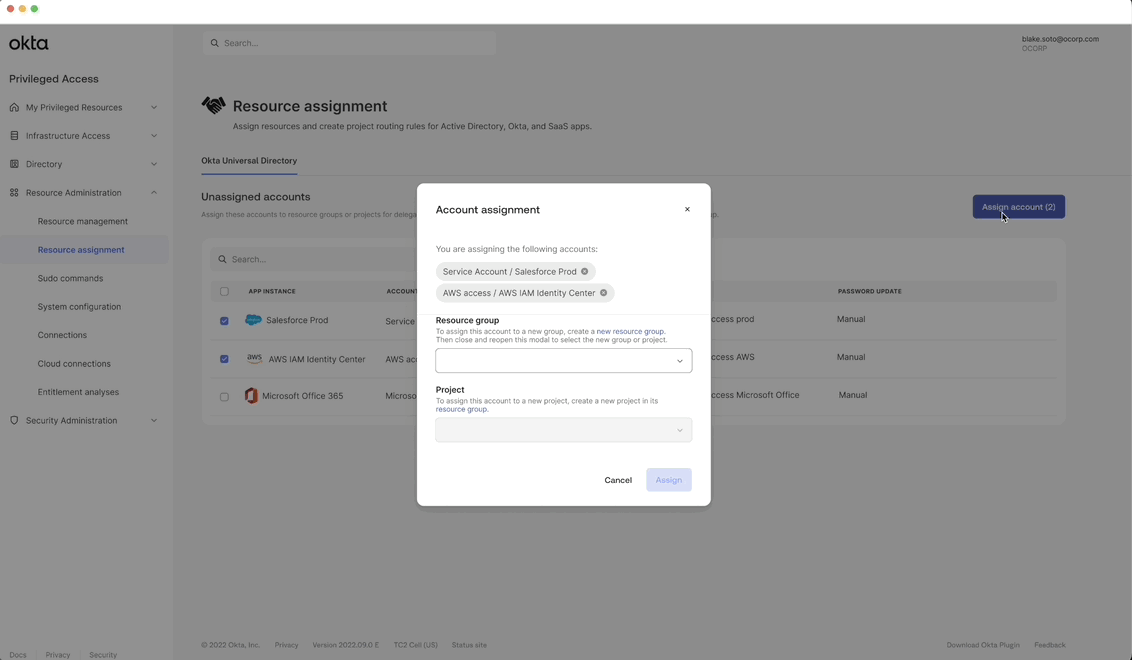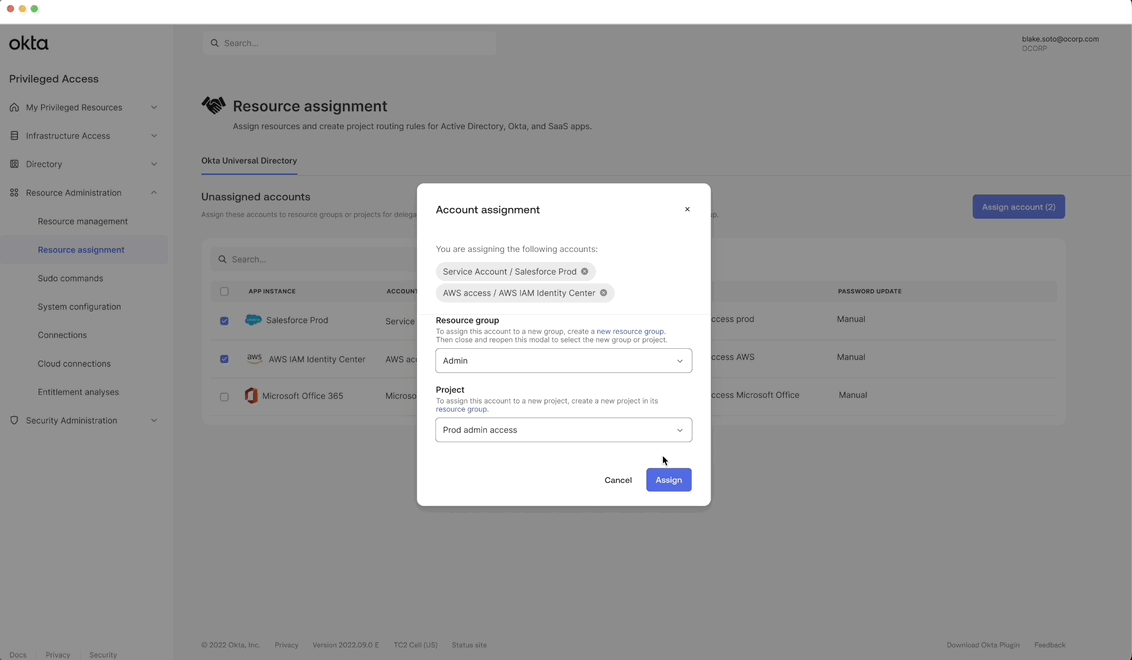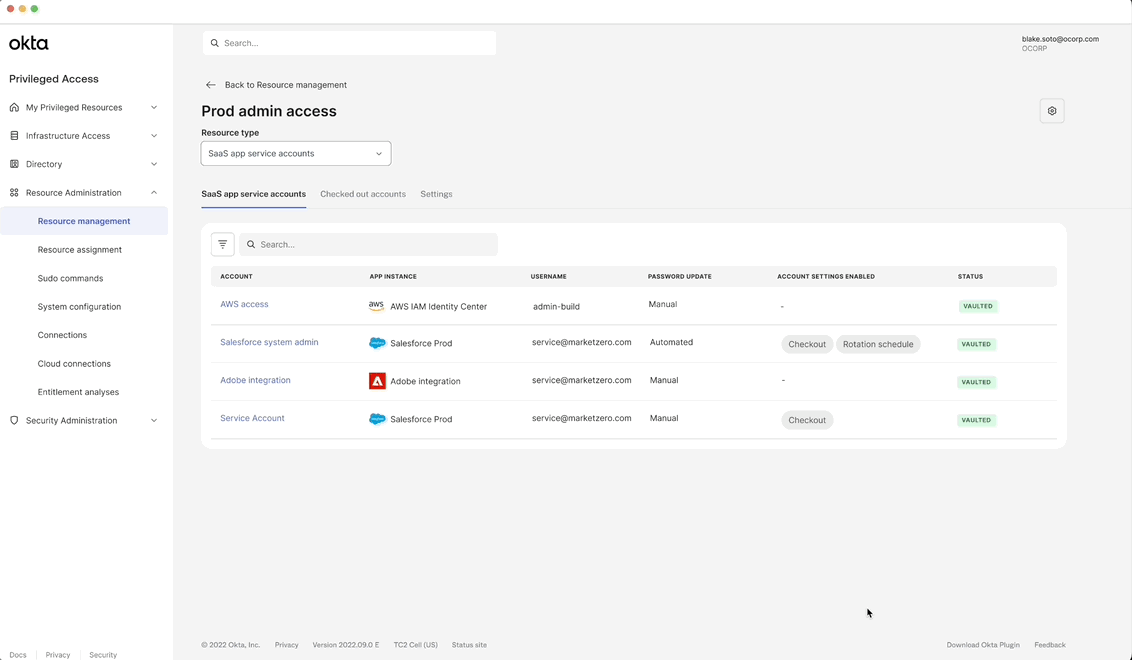
Centralized management of SaaS accounts
A single, streamlined interface that gives admins full visibility and control to view, assign, and manage all SaaS app accounts in one place.
Customer benefit: Eliminates the fragmented experience users were dealing with in their current process.
Creating a policy
Allow admin to create a policy to protect SaaS app account credentials.
Customer benefit: Allows admins to configure time-based access limitations as well as authentication requirements user were looking for like approval workflows, and MFA.
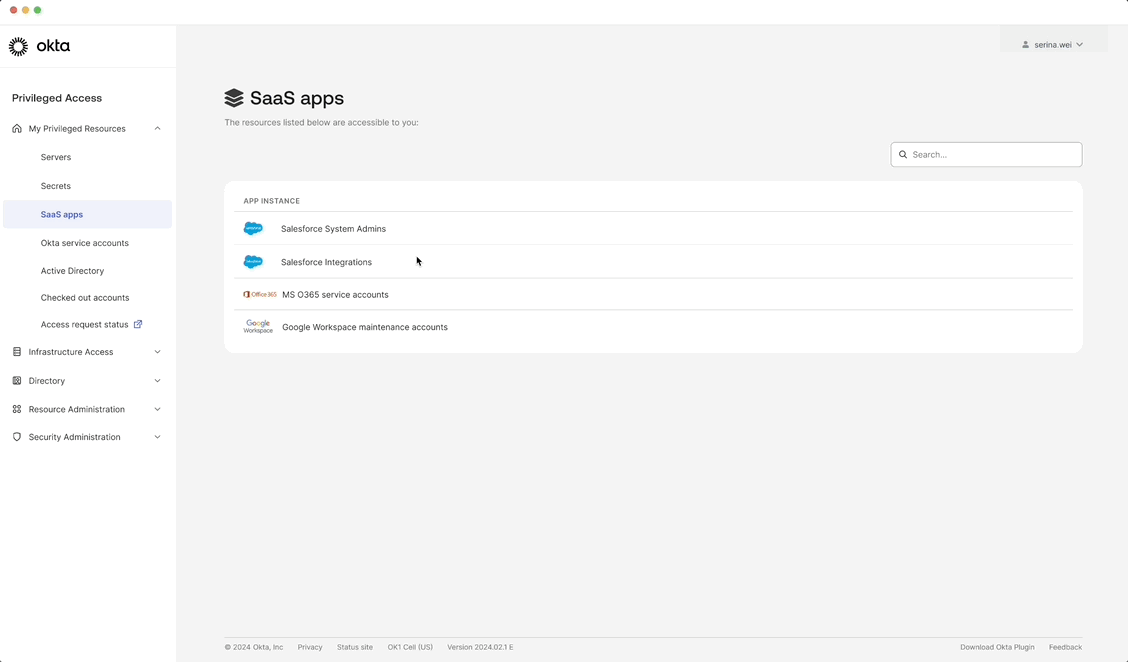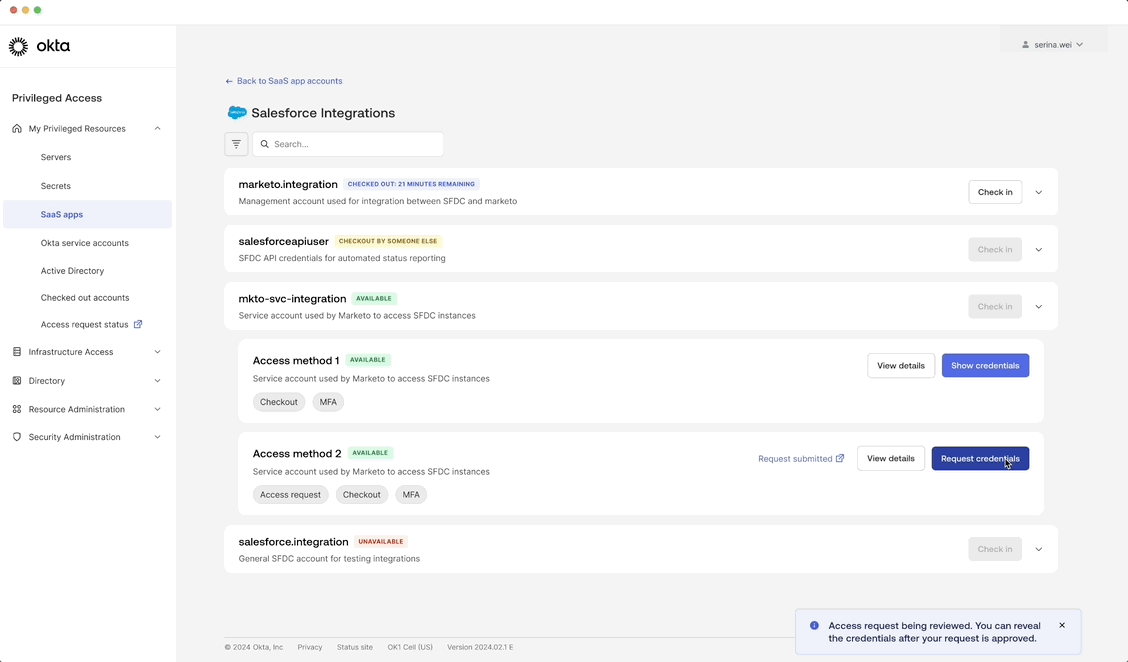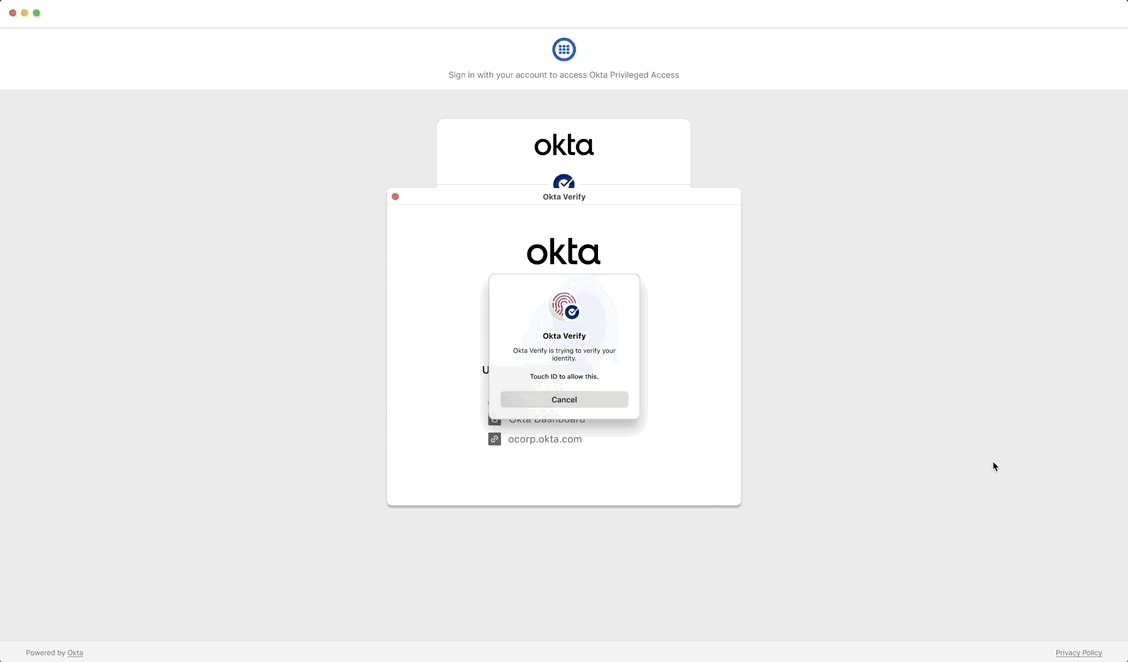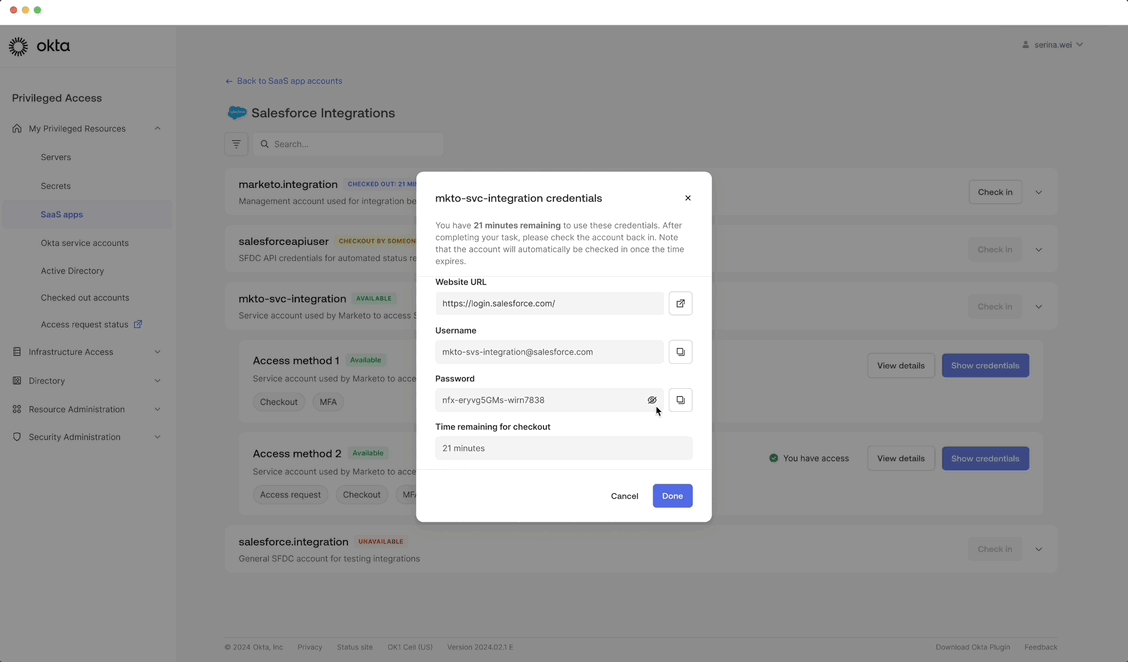
Accessing an account credential
End users may need to obtain an approval and verify their identity with MFA before receiving access.
Customer benefit: Enforces least privilege which limits access rights to only what’s necessary for specific tasks.
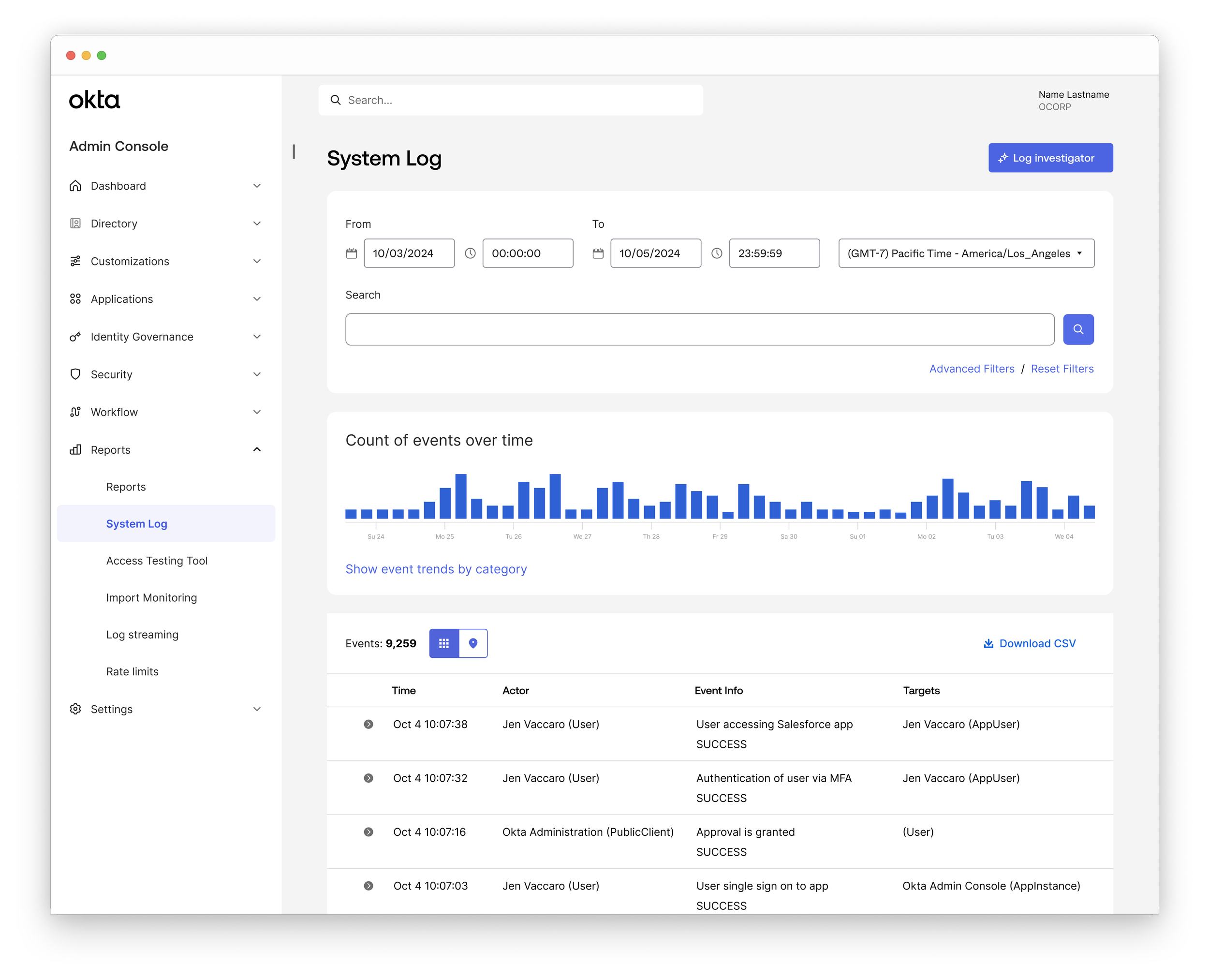
Audit who accesses which account and when
Admins can view an audit log that displays access events that includes user, specific action performed, guardrails, and timestamp.
Customer benefit: Gives admins full visibility into account creation and usage, enabling them to detect unauthorized access and meet compliance requirements.
Outcome
We provided secure access for end users, enforced compliance for admins, and drove adoption through a seamless experience.
After launching our solution, we closely monitored our success metrics to evaluate impact and identify opportunities for further refinement.
We were able to surpass all our initial targets 🎉
Overall, we received positive feedback from our customers post-launch.
“With MFA and access requests in place, most of our team onboarded quickly. And now we have full visibility into who’s accessing what. It’s a huge step forward in securing our shared accounts.”
- Security engineer
Learnings
Next steps
What’s next for us?
Here are a couple of enhancements to further improve this feature based on user feedback and ongoing research
Ability to move an account from one project to another
Discover accounts from more SaaS apps
Allow users to certify the accounts to make sure they are still needed
Browser plugin for single sign-on logins